How-To: In two hours, with no previous experience, you can build a "DNS Sink Hole" that can block ads, tracking cookies, popups, and email-trackers -- all by using a small $70 computer called a Raspberry Pi.
But most importantly, questionable sites, such as ransomware and other scams, are blocked at the network layer, long before your browser sees them.
This works for all devices in your network, including all desktops, laptops, phones, and tablets. You no longer need to install ad-blocking software. Benefits happen for all devices behind the router -- They do not have to be configured to gain the benefits.
Article updated on: 2025.0301 with newer software and installations steps. Added more screenshots.
This replaces a previous Keyliner article:
Stopping Tracking Cookies with whack-a-mole - blocking DNS using Acrylic DNS.
Related article: Build your own Internet-facing Webserver: https://keyliner.blogspot.com/2023/09/install-raspberry-pi-webserver-step-by.html
(This is a long article. But you can really do this in a few hours.)
The Raspberry Pi is a dedicated computer that handles all DNS (Domain Name Service) requests -- taking the function away from your existing routers. When an address, such as "keyliner.com" is typed, a request goes to your Domain Name Service. It translates the human-readable name into an IP address. If the address is nefarious, or an ad-network, the packet is discarded, keeping the traffic from reaching your device.
I consider a Raspberry Pi "Pi-Hole" crucial to my home network security.
As of this article, the "Pi" is blocking 246,000 domains. The chart shows the normal traffic at my house, with blocked requests in blue. Since last night, of the 13,000 requests, 2,500 were blocked (average 27% of all DNS requests are dropped!):
 |
| Click for larger view |
On an average day, the Pi blocks about 24% of all inbound traffic -- this is junk traffic that I have never missed.
Raspberry Pi, you say?
"I don't know anything about that!" Neither did I!
And yet, with zero experience, I built the server, installed Linux, and configured everything -- all in about two hours. The operating system and the soon-to-be-installed "pi-hole" software are free.
You can do this!
What is a Raspberry Pi?
A Pi is a small computer, the size of a deck of cards, running Linux, and costs about $60 to $70. It has 4 USB ports, an HDMI Video port, an RJ45 wired network jack, Bluetooth, a wireless adapter, and a slot for an SD-card.
Google-search to find a reseller I bought mine from Walmart.com. Any Pi version will work, where I am using an older version 3. Version 4 is newer (2023), and recommended.
There is now a Version 5 -- which is more power and costs than what this project needs.
You will also need the following:
HDMI cable to connect to your TV or monitor (temporary, just for setup).
With the newer Raspberry Pi models, this needs to be a Micro-HDMI to Full-sized HDMI cable.
Short .5 or 1 Meter (2 - 3 ft) Ethernet patch cable ($5)
Wired or wireless Keyboard (borrow from your PC, temporary)
Wired or wireless Mouse (borrow from your PC, temporary)
16GB (recommended) or 32GB Micro SD card, with adapter.
This is often included in the purchased Raspberry Pi kit:
Prerequisites:
You must be able to login to your router's admin screens before continuing. If not, consider this keyliner article, and this one. The person who setup your original network may be able to help with this password. Some routers will offer to reset the password after too many failed attempts (e.g.: Type the router's serial number, etc.), but this means re-attaching all wireless devices in the network. If you have to do this, be sure to write the new password down.
A. Identify a static (fixed) IP address
On your home network/internal network, find an address where the Raspberry Pi can live. Start by finding your local workstation's network IP-address range with these geeky but easy steps:
From a DOS / Command prompt (windows-R, "CMD"), type this command:
ipconfig (enter)
* Note your IPV4 address, illustrated.
Yours will probably read something like
192.168.100.10 or
192.168.1.17 etc.
The ".100" is the subnet. If the secondary (wireless) router has an IP Address of .2, ignore it and do all the work on the (.1) address.
* Note the Default Gateway's dot-1 address: (mine is 192.168.100.1) - This is your main router.
B. Test potential free / open IP Addresses:
Guess at an open address (in this same subnet) to see if it is free and available.
For example, pick this address: 192.168.100.151
-where that last octect is above (150) and below 254.
Test if this address is free:
From your workstation, launch a DOS prompt. Type this command:
PING 192.168.100.151
If no device answers, this address is safe. Otherwise, try a different near-by-number (.152, .153, 250, etc.). Write this address down.
(Subnets like 192.168.200.x, 192.168.1.x, 10.10.1.x are common. On those networks, PING 192.168.200.151, etc.)
Technical notes for those who care: Home routers assign automatic DHCP addresses to each workstation using a range (or pool) of numbers. This range varies by manufacturer. Some start at 2 - through 100, others start at 10 through 150. The range does not matter, but the Raspberry Pi needs a number outside that range, where I am choosing .151
You can research this by logging into the router. Type the "x.x.x.1" IP Address in a browser URL. A login panel appears. Login as "admin" and use the password the router was installed with (sometimes printed on the back of the device), or as set in your long-lost documentation. Once logged in, find an advanced setup menu for "LAN Setup" and "Use the Router as a "DHCP Server" (menus will vary). Confirm the exact DHCP Address range it uses, then pick a number outside of that range.
Continue with these software downloads:
C. Download and Install "Putty"
On your local workstation, download a small program called Putty.exe (a remote desktop console).
link: https://www.putty.org
Download and install. Program will be used later to help administer the Pi.
Place a tile on the start menu or desktop so the program is easy-to-find.
Install, but don't worry about how to use this program yet.
D.
Download and Install "VNC"
Although not needed for this project, on your local workstation, consider downloading and installing a remote desktop viewer
called "VNC". This can also used for remote administration - A remote desktop.
link: https://www.realvnc.com/en/connect/download/viewer/
Select Standalone EXE x64 Installer
Install, but don't worry about how to use this program yet.
Put an icon on the start menu.
-----------------------------------------------------------
Raspberry Pi Hardware Setup
Next, download and install the Linux operating system:
1. On your local workstation, plug in your SD-card Reader/adapter
If your laptop has a reader, use it.
2. Download the Raspberry Pi OS Installer
From a PC, Google "Raspberry Pi OS" download or this link
https://www.raspberrypi.com/software
3. Run the Pi Imager.exe program
In the Downloads directory, locate imager.exe
Right-mouse-click and choose "Run as Administrator"
*This does not install Linux on your Windows workstation. Instead, this is the program that writes the Linux "distro" (distribution) to your SD Card.
Select the device you are installing (Raspberry Pi 3, 4, or 5)
(look at your Pi's motherboard to see the hardware version)
Select the top Operating System, "Raspberry Pi OS (64-bit)"
Choose storage: (selecting the 16/32GB card)
Click OK/next
Choose "EDIT" on OS Customisation (British spelling).
In the OS Customisation menu,
Set HostName to "PiHole"
Set username to "admini"
Set password to ____________________
[x] Set Locale and Settings; keyboard layout
In the [Services] tab,
[x] Enable SSH with Password Authentication Important!
Click Save
Allow the SD card to write.
This takes about 10 minutes on a fast Internet connection
- Remove the Micro-SD card from the SD-adapter
- >Insert into the Raspberry Pi's card-slot
- The SD-card installs "up-side-down," into the board's slot
- Push until it clicks in place
6. Connect an HDMI cable to a TV or Monitor
(I used my TV).
- Connect a USB Keyboard to the Pi's USB ports (borrow from your desktop; can be wireless)
- Connect a USB Mouse (can be wireless)
- For the initial setup, use either a wired or wireless
connection. Wired is preferred.
For a Wired RJ45: If near the main router, connect an RJ45 network cable to any open port on any router. (Do not plug into the router's "uplink" port; instead plug into one of the 4 or 8 port areas). Connect the other end to the Pi's RJ45 port.
If Wireless, continue with the USB power supply step; later connect to the wireless network.
- Connect the USB 2.5a power-supply to the Pi. (Any 2.5a micro-USB cell charger will work. Usually supplied in a the Pi-kit.)
The Raspberry Pi will boot (visible on TV or monitor). You may need to switch the INPUT to find the right HDMI port.
---------------------------------------------------------------------------
Raspberry Pi Operating System Install
---------------------------------------------------------------------------
When the Pi first-time boots with the new SD-card installed, it arrives at the Linux desktop. This will take several minutes for the first-time boot and there will be lots of screen blinking.
Select the Raspberry icon
Preferences
Raspberry Pi Configuration
In the [Interfaces] tab
Turn on SSH
The goal: set the Pi to a static (fixed) IP address:
See: Advanced Options, Edit Connections
Select "Ethernet, Wired Connection 1"
Click the gear icon
In IPV4 Settings, Add a new address.
In the three horizontal fields, type these values:
Address: (see above, e.g. 192.168.100.151)
Netmask: type "24" (or 255.255.255.0)
Gateway: 192.168.100.1
Save and Close the window
C. Return to the upper-right up-down arrow menu: "Turn Off Wireless Lan"
(this assumes the pi is connected to an RJ45 Wired Network Connection)
Note: You can continue to use wireless for the initial setup. If so, also set the wireless IP to this same address, but once this box goes into production, it really needs to be on a wired connection.
Login again.
From the desktop, launch the chromium browser and confirm you can see the Internet (open Google.com or something).
E. Update / Patch the OS
In the top, left-side menu, near the Raspberry icon, locate the "terminal" icon. This opens to a DOS-like screen. Update the Pi's OS with these case-sensitive commands:
sudo apt-get update
sudo apt-get upgrade -y
Testing:
F. Test Putty
From your Windows workstation, launch "putty.exe"
In the Host Name or IP Address, type "192.168.100.151" (or "pihole.local")
You will be prompted, "This is a new connection. Do you trust it?"
Login using "admini" and the password (case-sensitive)
This confirms the program works. Close the Putty window.
G. Optionally, test VNC Remote Control Software
VNC is a remote desktop (which is different than the Terminal) and it lets you see the Pi's actual desktop from your Windows workstation.
First, enable the VNC service by logging into the Pi-server (using Putty, or from the server's desktop "Terminal" program). Login to the server as "admini".
1) At the command prompt, type
sudo raspi-config
2) From the DOS-like menu, select "Interface Options";
Select 'Enable VNC' (not illustrated).
Press Esc a few times to save the changes,
then close the (putty) terminal window
3) Continue from your local Windows workstation:
Launch the previously-installed Windows application "VNC" (Real VNC)
Select the small link at the bottom of the screen, labeld: "Use RealVNC without signing in"
(You do not need to register or login to their website to use this program.)
4) Create a new connection by typing "192.168.100.151" (or "pihole.local")
Accept "VNC Server not recognized...do you trust this..."
Confirm you can see the desktop. Wiggle the mouse, browse, etc..
Close VNC
VNC seems to have a bug and will not connect a second time using the same configuration. To reload the desktop's VNC connection, delete the previously-built ".151" connection and rebuild each time needed. Unclear how to resolve this or what I am doing wrong. My expert friend says use a different program than VNC, but VNC seemed the easiest to install.
Woo-Hoo!
Congratulations. The Raspberry Pi's Operating System is installed and is ready for the Pihole software.
The next step installs the Pi-Hole DNS Server software.
--------------------------------------------------------
Install Pi-Hole DNS Software
---------------------------------------------------------
Once the operating system is installed and patched, install the Pi-Hole software:
1. Open a Terminal Window and install pi-hole
Using either Putty.exe or the Raspberry Pi's top-menu, open the "Terminal Window" (command prompt)
- Type this case-sensitive command.
curl -sSL https://install.pi-hole.net | bash
Note the split-vertical bar
The install begins with this panel:
2. Answer these prompts:
"This installer will transform your device into a network-wide ad-blocker"
ENTER for OK
- At the "Static IP Needed", press tab <Continue>
- Choose eth0 for the hard-wired port
(This must be selected even if using wireless during the base install)
- Accept Google (or OpenDNS) as the upstream DNS Provider
I prefer Google, knowing the Pi subscribes to the same lists as OpenDNS - On the "Blocklist" panel, select "Yes" to accept the default list. This will be modified later in the install.
- Use Query Logging? (Choose "Yes')
- Select Privacy Mode for FTL: Select (*) Everything
3. At the "Installation Complete" message (wait for this prompt),
Important: Step away from the keyboard.
This is the dashboard's "admin" userID and password (different than the Pi's default "admini" userID)!
This dashboard/admin password will be changed in a moment.
Dashboard Password example:
192.168.100.151/admin Password: xxxxxxx______________________
Click "OK" (but wait on restarting)
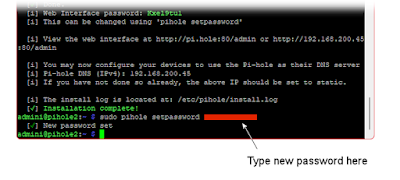
4. ! Change the Pi's dashboard admin password
Do this now, while you are at these screens:
From the main desktop, open a terminal window.
Type this command at the terminal prompt:
sudo pihole setpassword (type your new password here)
(Recommend making it the same as the admini / root / SSH password.)
The Pi-Hole hardware is now ready to use. A moment of self-congratulations is in order. Wiring work, and router-steps are still required.
Write this stuff down!
PiHole Server IP Addr:
__________________
(recommended: xxx.xxx.xxx.151)
PiHole Server Name:
pihole.local
PiHole SSH Admin User ID:
admini_
PiHole SSH Password:
PiHole Dashboard (web) Password:
(login at xxx.xxx.xxx.151/admin not 'admini')
__________________
Router / Gateway Address:
__________________
(usually xxx.xxx.xxx.1)
Router Login:
__________________
(usually admin / pwd)
Final Pi (Production) Wiring Steps
Using the top-Raspberry menu, shut-down the server.
Unplug the HDMI cable; The monitor is no longer needed.
Unplug the Keyboard and Mouse; these are no longer needed.
a. Move the Raspberry Pi to a location near the main router.
b. Using a short Cat-5 Network cable, plug in the Raspberry into any available port on your router or other network hub. The Pi does not have to be directly plugged into the main router; it can use a downstream router if you have more than one. Important: A hard-wired connection is required.
-- any open port can be used, where there are groups of 4 or 8 network jacks. Do not plug it into the up-link port (a lonely port, usually a different color - yellow):
Give the Pi a minute to boot and get settled.
Note the activity lights on the Pi's RJ45 network port.
From your PC-workstation, open a DOS / Command Prompt and ping the Pi to see if it is on the network. Type this command:
PING 192.168.100.151
Expect a reply in xx milliseconds.
Pi Administrative Dashboard Login
---------------------------------------------------------------------
Test the administrative dashboard login
From any browser, type the Pi's IP address/admin:
192.168.100.151/admin
You will be prompted: "Warning: Potential Security Risk"
Click Advanced and accept the risk.
At the main admin Panel, a dashboard displays.
Note: There is no activity until the Routers are changed -- see next steps.
Update Gravity
From the Pi's admin panel, glance at the upper-left, "Domains on Lists"
If the count is zero or there is an error,
 |
| Click for larger view |
Close the browser window. Continue with the Router setup steps.
Router Setup
--------------------------
The final step is to configure the router(s) to point to this new Domain Service.
These changes are required in order to activate the Pi.
This is a one-time setup.
For most households, the main DSL or or wireless router (the box with a ".1" IP address) is the one to change (this would not be the Cable Modem). Some networks may have a larger, secondary wireless router, where all devices and hubs are connected. If so, use that device. See your prerequisite checklist.
1) Login to the main (wireless) router's (.1) address (as tested in the per-requisites, above)
From any browser, type the main router's address in the URL address bar.
For example: 192.168.100.1
192.168.1.1
This is not the Raspberry Pi's IP address.
The Login ID varies by product/brand.
Login using (typically) "admin" or "administrator"
and the previously-recorded router password (not the Pi's administrative password).
2) Change the router's DNS settings
Once logged in, the main setup screens vary by modem manufacturer.
Several example routers illustrated:
- Usually under an Advanced Configuration menu
- Look for a DNS Setup section (or sometimes DHCP/DNS)
- Look for
"Dynamic DNS" (or "Auto-DNS", or "use these DNS Servers", depending on modem)
- Change to:
either "Static DNS" or "Use these DNS Servers"...
- At the Primary DNS, type the IP address of the Raspberry Pi.
For example, on my network, 192.168.100.151
(This is the Pi's IP Address; must be in the same subnet (.100) as the router)
3) Set the Secondary DNS.
If possible, and if the router allows, leave the secondary DNS blank.
If the router requires a secondary address, do one of the following:
type 192.168.100.151 (duplicating the Pi-hole's address)
or type 127.0.0.1 (a dummy address)
either idea is acceptable.
Optionally, for the secondary DNS, put in this address:
208.67.222.222
-- This is OpenDNS's DNS server -- they are a third-party pi-hole-like DNS provider, doing many of the same features as the PiHole.
And finally, with reservations, the secondary DNS could be set to
Google's DNS: 8.8.8.8
Do this before moving to any other screen.
The router will reboot.
Other Example Modem Screens:
Zyxcel DSL router looked/s like this:
* Some of newer models of routers require a secondary DNS
If using Google's 8.8.8.8 as a secondary DNS, this is redundant because this is the go-to address used by the Pi. In this router, which requires a secondary, I would type 127.0.0.1
* As another example, a typical older Linksys router looked like this:
* A NetGear Genie AC1450 looked like this, where the Raspberry Pi was the primary and again, Google's DNS was set as a secondary (not recommended):
(end of examples)
Other Devices
Most computers and devices on the network (desktops, laptops, tablets, phones) automatically connect using DHCP. They get their address and domain services from the router. No other action is needed. They automatically pass through the Pi, with the router telling them who their DNS provider is. This includes cellphones, tablets, etc.
** If you have a device with a hard-coded IP address, typically a printer or SAN drive, then manually set that device's IP Address, Subnet, and DNS, setting the DNS to Google's address: 8.8.8.8. Practically speaking, for the DNS, you could use the Raspberry Pi's address (e.g. 192.168.100.151) -- but these devices do not surf the web, and dumb humans are not doing anything strange on them. My Printers and Network drives bypass the Pi.
Raspberry Pi and Pi-hole configuration is complete!
TESTING
To properly test the new PiHole, you must disable the workstation's locally-installed ad-blocking software (uBlockOrigin, and others). Reason: Ad-blockers also block traffic and it is hard to tell who did the blocking. The difference is they block the traffic *after* it has downloaded where-as the Pi keeps them from ever downloading.
You may or may not have ad-blocking software installed. Look in your browser's Tools, Add-Ins menu and look for "adblock-plus" or "uBlock Origin" (the two most commonly used blockers).
Example: Extensions in Firefox (Extension Manager), where uBlock has been temporarily disabled:
This is an advertisement and likely that ad is recording your PC's IP address and other information. The 'page not available' message is the Pi-hole at work, discarding the traffic. This is good.
Each application or browser decides how to handle the "error" in its own fashion. Many show empty white-space where the ad lived -- with no obvious errors.
The neat thing about this is the vendor never knew you attempted the connection because it is blocked before the traffic left the house. You won't be tracked, monitored, or recorded as you read articles, and big advertising graphics won't download.
Test 1:
This test makes sure the network is functioning properly and you have the routers pointing to the right DNS-resolver (the Pi-hole).
- From your normal workstation, browse to www.google.com
- If you arrive, the pi-hole / DNS is working correctly
- It saw the DNS request, saw no issues, and passed it through, un-impeeded
- Browse to Yahoo.com(Update: Yahoo has cleaned up their page since this article was written and most ads are now within their own yahoo.com domain and are not blocked by the pi-hole because Yahoo got wise to this and other ad-blockers.)Where I really see ads being blocked in on the cellphone while reading news articles.
- Note "holes" in the page -- blank spaces, illustrated below in orange. There are being snuffed by the Pi-hole. (some browsers treat this differently, not showing the holes). Later, from the Pi-hole admin screens, you can temporarily disable the Pi, and can see what the page looks like, before-and-after.
- Be sure adblockers are disabled or this test will be distorted.
- Note "holes" in displayed page. These are never transmitted; speeding up page-loads. The drawback is content providers cannot monetize their content. There are moral and ethical considerations; see the end of this article for a discussion. On the other hand, they are often abusive and can (accidentally) provide malicious content.
 |
| Click for larger view |
Test 3:
- Attempt to browse to https://190.com - a nefarious site
- Note how pi-hole blocks the address. It may look like this, or this, depending on your browser:
or this:
or if you have an ad-blocker installed, and it were still active:
- Browse to "didtheyreadit.com" (an email tracking service). As-of this article, you will likely succeed and arrive at the site. Consider "Blacklisting" this and other such sites. See the blacklist later in this article.
- Note that *all* devices in your network benefit from the Pi. And, more importantly, none of the devices need to be told about the setup -- it just works. But if your device (cell phone, tablet, laptop) strays from the network, the Pi's benefits are lost.
Side-notes: If the domain is on the naughty-list, the Pi dumps the DNS request into a dark hole, hence "pi-hole." As of this article, I've added 240,000 domains in the discard list. If the address is on the good-boy list, it is handed off to to your default (Google's) Domain Services. (Google) resolves the address normally.
Testing: Simulate a pi-failure:
Unplug the Raspberry Pi's power and attempt to browse any site from any workstation.
Assuming the routers have no secondary DNS, you will find Internet addresses do not resolve*. In other words, the Pi is required to be online -- just like the router is required to be online.
Restart the Pi and give it a few minutes. Repeat the test, confirming the network returned to normal.
Testing: PiHole Administrative screens:
On the administrative screen (login to 192.168.100.151/admin)
Select "Recent Queries" to see a log of recent activity can be reviewed.
You will be amazed that after a few random minutes of surfing, from any device in the network, the blocked DNS traffic. Illustrated, my "smart" TV is busy on the network, playing Pandora, and I caught a Nest Thermostat checking on the daily weather. This traffic was allowed to pass.
 |
| Click for larger view |
But "settings-win.data.microsoft.com" was blocked. This is Microsoft collecting diagnostic data for the Consumer Windows Experience program; see link Infoworld article. The Pi-hole team decided this was intrusive, and added this address to the blocked domain list. From the admin panel, it could be white-listed with a click.
What happens under the hood:
When a device tries to resolve a blocked domain name, the DNS service drops the request in the hole and discards it. The page does not even know a call was attempted. No graphics, scripts, or other code runs from the discarded site. Similarly, if a page has embedded code that reaches out to other (blocked) third party domains, those domains are dropped; the code will think no network was available. This is a win-win for you.
There are two other areas of particular interest: White and Black lists.
White Lists:
For sites where you want to support advertising, such as the NewYork Times, allow them their ad-revenue by adding their domain to the Pi's white-list.
See the dashboard's left-nav, "Domains".
When adding a domain, always select [x] Add domain as Wildcard
Choose "Add to WhiteList" (or "Add to Black list")
If you decide to keep your browser's ad-blocking software installed, you will have to add the site to both the Pi-Hole's white list and your local ad-blocker's white-list.
Regardless of who you want to support, for technical reasons, add these domains to the Pi's whitelist ("Allowed domains")
* When adding, click [x] Add domain as wildcard
+ nexus.officeapps.live.com (Outlook; Media Player)
+ redire.metaservices.microsoft.com (Windows Media Player)
+ d2avsp0hxzxate.cloudfront.net (something Apple needed)
+ statcounter.com (if you track your own site's traffic)
+ trackcmp.net
Blacklists allow you to add your own bad domains to the pi-hole, even if the pi-hole's adlists are not blocking the traffic. I manually add the following to my Pi-hole Black List -- especially Email tracking addresses.
These are addresses I have discovered and they were not on the Pi's official lists (as of 2019.10). Some sites are now on the Pi-block lists. It does not hurt to explicitly add them.
See the dashboard's left-nav, "Domains".
When adding a domain, always select [x] Add domain as Wildcard
Choose "Add to Denied Domains" ("Add to Black list")
Type each address manually (without a "*" wild-card symbol):
When black-listing; always add as a "WildCard":
123banners.com
l90.com
adforce.com
advertising.com
agkn.com
appnet.com
assia-inc.com #seems to be a tracking site
avenuea.com
babator.com
bananatag.com #email tracking
bluekai.com
bluestreak.com
burstmedia.com
burstnet.com
cdn.nmcdn.us #click bait
clearslide.com #email tracking
clipix.com
cloudcheck.net
contactmonkey.com #email tracking
crownpeak
deskun.com #email tracking
didtheyreadit.com #email tracking
doubleclick.com
doubleclick.net
dynamicyield.com
engage.com
evidon.com
exelator.com
extreme-dm.com
fastclick.net
filepicker.io
g2crowd.com #email tracking iko system also velocify
getnotify.com #email tracking
gigya.com
gmelius.com #email tracking
gobankingrates.com
go.com
hubspot.com #email tracking
icanbuy.com
imgis.com
imrworldwide.com
intelliverse.com #email tracking
keywee.co #Note the .co, not .com
livehive.com #email tracking
mail-track.com #email tracking
minute.ly
newtonmail.com #email tracking
nr-data.net
optimizely.com
outbrain.com
outreach.com #email tracking
pagefair.com
pixelsite.info #email tracking
pubexchange.com
quantserve.com
remail.com #email tracking
remail.io #email tracking
rlcdn.com
rocketbolt.com #email tracking
ru4.com
salesloft.com #email tracking
sidekick.com #email tracking, now hubspot
saleshandy.com #email tracking
scorecardresearch.com
stats.net
streak.comp
sync.optimatic.com
taboola.com
teknosurf.com
tinypass.com
toutapp.com #email tracking
tru.am
valueclick.com
velocify.com #email tracking Velocity Pulse
voicefive.com
websidestory.com
w55c.net
yesware.com #email tracking
Subscription Additional Recommendations:
As of early 2025, the default pi-hole installs with this subscription list, seen during the base-install:
120,000 items. See left-nav, "Lists" (subscribed lists / add blocklist):
https://raw.githubusercontent.com/StevenBlack/hosts/master/hosts
Some of these lists are specific ("Click Bait sites in Japan"). Some are too short to bother subscribing and if interested, simply add the list manually to your own black list. For compatible lists, look in the Software column for the Raspberry Pi icon (see illustration directly below).
Keyliner also recommends adding other lists:
https://raw.githubusercontent.com/badmojr/1Hosts/master/mini/hosts.txt
To add other lists:
a. Browse filterlists.com;
b. When a list is found of interest, click right-nav "View" to examine
f. Paste the URL; Select AddBlockLists
Often, there is overlap between these lists; no harm. They are maintained by volunteers.
Once all lists of interest are added:
From the Dashboard, note the new number of Domains on Block List
De-Installing Pi-Hole:
To temporarily disable the pi-hole (for testing a blocked site):
- From the admin screen, left-nav, click "Disable Blocking"
When disabled, all requests pass through to (Google's) DNS service, and all Pi-protection is lost. Note: This is not your router's secondary DNS setting, this is the Pi-Hole's default DNS resolver: 8.8.8.8.
To permanently remove the Pi-hole from the network:
- Login to your router's .1 address
- Change the Static DNS field
from (192.168.100.151)
to Google's DNS: 8.8.8.8
A worse choice would be to return the Routers to "Auto-DNS" -- this would put you at the ISP's mercy.
Click "Save". The router will reboot.
Once changed, the Pi can be unplugged and removed from the network. No workstations or other devices need to be told of this change. The devices will need to reboot one time.
Known Problems:
Some sites, especially those that show the "top 100 celebrity before and after photos" will be blocked. Reason: These are trolling sites, with obtrusive ads and with possible fly-by virus installs -- my good friend just got hammered by one of these. If he had a Pi running, he would be safe. In any case, these sites were deemed dangerous, and were blocked by the Pi-hole community. Trust their decision.
For the first few months, every other type of web failure will be blamed on the Pi.
My experience is the Pi has not been wrong. The blocks were legitimate.
To test if the Pi is causing a problem, use the admin screens to temporarily disable the Pi-hole (see left-nav, "Disable"). Ctrl-F5 to flush cache, then re-test the site or page in question. The Pi is innocent if the site still malfunctions and this might be a browser or server problem. The Pi does not interfere with non-blocked sites.
But, if the Pi blocks the site, it has a reason for doing so. If you trust the blocked site, and insist on arriving (overriding thousands of volunteer's opinions), add the domain to the white list.
Updating Pi-Hole Software
----------------------------------------------------
A. Login to the Linux Raspberry Pi desktop with either Putty or DOS SSH
With Putty, login to "pihole.local" (or 192.168.100.151)
UserID: "admini"
or, with DOS, type "SSH.exe admini@192.168.100.151" (no quotes)
B. At the "admini@pihole:~ $" prompt, update with this command:
type sudo pihole -up
Once or twice a year, I recommend doing an update.
On 2025.0228, I ran the sudo Pihole -up command; the install ran to about 90% done, then crashed -- saying the Linux OS was too old. The Pi had to be rebuilt. Not that this was a big deal; this article gave the steps and it took 45 minutes to get back online. Obviously, the upgrade should have checked the OS first, but it would have been the same work. This was a good time to update this article.
2025.0419 sudo pihole-up ran without incident
Alternatives to the Pi-Hole:
---------------------------------------------------------------------------
An alternative is to use OpenDNS's IP addresses as your router's primary and secondary DNS.
Instead of the pi-hole, use OpenDNS with these similar steps:
- Login to your .1 routers, as described above.
- Change the primary and secondary DNS address from your ISP's address, or from the pi-hole's 100.151 address, to OpenDNS's addresses:
Primary: 208.67.222.222
Secondary 208.67.220.220
These addresses are also an option on the Pi-Hole installation screen, where you can pick OpenDNS, or Google's 8.8.8.8 address as the final arbitrator for downstream DNS name resolution. Using both the Pi and OpenDNS is redundant.
The Pi is a tad faster, and has white-listing and blacklisting overrides, which OpenDNS does not without costs. See the comments at the end of this article for more discussions. Plus, I think the Pi community is more dynamic and more active.
OpenDNS has a different free version, called "FamilyShield", which uses these addresses to block all of the above, plus Porn, and Proxy Servers.
- 208.67.222.123
- 208.67.220.123
Pi-hole and Ad-blocker Ethics
------------------------------------------------------------------------
A word about publishers who use revenue to keep producing content. Ad-blocking, and the Pi-hole, cut into these revenue streams. But the current model of using third-parties to display ads is broken.
You might want to let the New York Times broadcast ads, but the ad-sites are often third-parties, and can be untrustworthy. Case-in-point, my friend browsing The Washington Post, when he clicked a "click-bait" article at the end of a news-feed and immediately lost his computer to a virus. "It took about a quarter-second, and boom, it was gone."
Many publishers detect ad-blockers and refuse to display content. The Pi-hole can sometimes dance around that restriction. In other words, disable the locally-installed ad-blocker, and let the pi-hole sink the DNS requests undetected.
The industry has matured and many publishers now host the ads on their own sites, using their own domains. If the Washington Post domain is blocked for the ads, it also blocks the content, and the Pi and all ad-blockers are ineffective.
The other side of this argument is obvious: Publishers and Advertisers have abused ads by displaying full-screen, non-dismissable ads, and by breaking articles into dozens of pages for ad-impression rates. These are why the pi-hole exists and these sites deserve to be blocked.
Related Security
-----------------------------
If you are running Firefox (and likely Chrome and Edge), consider installing these security extensions. These compliment the PiHole but are not required for this project:
Be aware that uBlock Origin (one of the best ad-blockers, running on the local machine, and not available to tablets or cell phones) has been severely hampered by Google's changes in the Chromium browsers. Google claims the API's that UBlock calls need to be disabled for security and other reasons; others think Google wants to protect their ad-revenue. The Pi is immune to this problem. And Firefox is not a Chromium browser.
-----------------------------
Related Keyliner Articles:
This is the way I used to do this -- manually blocking about 50 high-volume sites. With this article, I now block 125,000 sites!
Stopping Tracking Cookies with whack-a-mole - blocking DNS using Acrylic DNS.
Learn more about the pi-hole project here:
https://pi-hole.net/2018/01/11/pi-hole-is-open-source-consume-contribute-or-both/#more-9734
and
https://pi-hole.net/2017/05/12/seven-things-you-may-not-know-about-pi-hole
Related Thoughts:
Some routers run Linux under the hood and can be re-programmed to run a pi-hole directly on the router. After reading this article, https://www.ab-solution.info, my co-worker tried this. The router seems to be the best place to run this type of process, but not all routers can be re-programmed. Doing this takes skills which are more simply done on a Pi-hole. Ultimately, he reported back (unspecified) troubles, and abandoned the idea, returning to the Pi-hole.
Your comments:
I would like to hear your comments on this project.
If you like the Pi-hole, donate a few dollars their way; they deserve the support. See the admin-login screens.
History:
2017.11 Initial Install
2018.03 Pi-hole intercepted an email phishing site. Saved the checkbook
2019.01 Rewritten and updated this article. Donated to PiHole project
2019.10 Improved grammar; an editor's work is never done
2020.02 More editing. Dang, this article was hard!
2021.02 More editing. Dang, this article is still hard
2021.02 Donated to PiHole project. Running 4 years, no issues. Bought a newer pi..
2023.09 Six years. Zero problems. Not even a hiccup. Amazing. Noticed a heatsink fell off
2025.02 Upgraded with pi-hole -up and crashed the server. The first problem in 7 years. Had to rebuild the pi. It needed it anyway. It took 45 minutes.
----------------------------
Now obsolete notes:
Some versions of the Raspberry Pi operating system have other pre-installed software; often these are called "Noob" installs. Much of the software that comes with these 'distros' can be removed with these steps.
-Update: Newer Raspberry OS installs (Debian), do not contain these distros and this step seems obsolete.
Optional Cleanup Steps:
The operating system comes pre-installed with extra software that is not needed for this project.
From the main Linux desktop, top-menu, open a Terminal Window.
Type these commands, pressing ENTER after each.
Answer with "Y" (capital Y), when prompted.
If software is not found, press the up-arrow and double-check the spelling, or move to the next command. Note: In many of these packages are no longer installed in some versions of Linux. If not found, don't panic and move the next one.
a. sudo apt-get purge wolfram-engine
b. sudo apt-get remove --purge libreoffice*
c. sudo apt-get purge sonic-pi
d. sudo apt-get purge scratch
e. sudo apt-get purge greenfoot
f. sudo apt-get purge geany
g. sudo apt-get purge nuscratch
h. sudo apt-get purge python-pygame
i. sudo apt-get purge pygame
j. sudo apt-get purge squeak-vm
k. sudo apt-get purge dillo
l. sudo apt-get purge minecraft-pi
m. sudo apt-get purge penguinspuzzle
n. sudo apt-get purge oracle-java8-jkk
o. sudo apt-get purge oracle-java7-jdk
p. sudo apt-get purge openjdk-8-jre
a. If one or more of the above were successfully de-installed:
- use the top-menu to reboot the Pi.
Then issue these commands:
sudo apt-get clean
sudo apt-get autoremove --purge
(The command will inform you if it is up-to-date)
sudo apt-get update
sudo apt-get upgrade -y
Optional software is now de-installed.
Approximately 2G of disk space is freed.
-This completes this article.