Midy5 - Show a file's MD5 or SHA-256 checksum
An MD5 or SHA-256 is a calculated values of a file's checksum and can show if a file has been modified. The checksum is like an encrypted hash or fingerprint that identifies the file. All files have this unique key.
Use this free keyliner utility to display the file's internal checksums, showing both the MD5 and the SHA-256. The program is affectionately named "Midy5".
 |
| Click for larger view |
(MD5 is an older style; SHA-256 keys are more cryptographically secure. This program shows both.)
No registration, no login, no required email.
No advertisements, no nags, no spying. Does not call the mothership.
Free for personal and commercial use.
The Need:
Often vendors publish the checksum for their files. When you download the file, say from Source Forge, or other distribution sites, compare the original vendor's published MD5 with your copy. If different, you know the
file was changed and the download should be viewed with suspicion.
For example, a picture's MD5 checksum might be
File: SomeFile.png
MD5: f2-4b-ae-fc-37-e8-85-a5-0e-41-3a-3e-9a-60-3a-d0
Changing one-pixel from a ghostly-light-gray to white results in a wildly-different MD5-hash:
MD5: 33-94-8b-b0-82-bc-a2-f4-e2-51-35-43-8f-ae-dd-a9
Files copied to a different drive, will get a different date-stamp, and the file can be renamed, but both copies retain the same MD5 / SHA-256. By looking at the hash, you would know they were identical files.
Checksums can also show if a file was corrupted or changed by other legitimate processes since it was last checked. A file re-copied (with new date-stamp) may be the identical file, or may be changed. The checksum is able to tell.
Midy5 Features
- Retrieves any file's MD5 or SHA-256 checksum
- Results can be copied to the clipboard
- Drag-and-drop files from File Explorer, or browse to the file
- Pass filename from the command-line
- At a glance compare two files checksums, Date-time, file size
- A small executable, fast, easy-to-use
Installation Steps:
No advertisements, no nags, no spying. Does not call home.
Free for personal and commercial use.
keyliner does not (and cannot) track who downloads or runs this program.
Installation
is easy: Download the .exe and place in any folder on your hard disk.
Double-click the .exe to run - no installation required.
Since
keyliner cannot afford a signing certificate, you will be prompted that
the file is not safe (being downloaded from the internet). Click "more
information" and allow the program to run.
Follow these steps for a more professional installation:
Using the .exe from a download folder, or copying to (my Documents) folder is
a quick workaround for various Windows 10 and 11 security concerns. Some vendors recommend this, but these folders are inappropriate for executable
software. Instead, the program should be copied to Program Files so it gains the
protection of other Windows security features. Total time: about a minute.
A. Download the .exe to a Download or Temp folder:
From Keyliner's public GDrive, click this link and download to a local temp or download directory. Do not download directly into ProgramFiles.
Download Link
https://drive.google.com/file/d/1QGeawJH9v0HrbsFqwg1z-WNd8kxeNcuA/view?usp=sharing
Ironically, I used this program to publish the download's own MD5:
Midy5.exe, Version 1.04
MD5:c3-19-68-a8-9b-5e-c0-c2-81-74-f7-5e-3d-8a-74-55
SHA256: 0f7f278d8f90aa8616eeb1bd0c392a065bd4c63338ee423c306f5a504a1d9427
When downloading, different browsers behave differently.
You will be prompted 'file cannot be scanned.' Click "Download anyway".
For, example:
Microsoft Edge Downloads:
Prompts "Midy5.exe was blocked because it could harm your device."
Click "See More" and allow the download.
With Edge, the file appears in your Downloads directory with a random name, "Unconfirmed 780359.crdownloaded" (name varies).
Use File Explorer to rename the file to "Midy5.exe".
B. Mark the program as safe-to-run:
(This step may not be needed if downloaded by Edge and you clicked "More / Download Anyway")
Using File Explorer, right-mouse-click the downloaded (and re-named) Midy5.exe
Select "Properties"
Check [x] Unblock. (This removes the "mark of the web.")
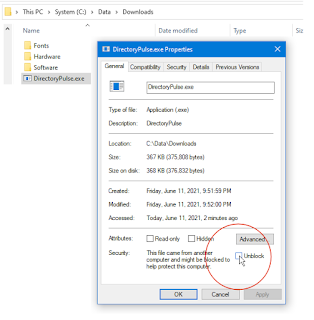 |
| Click for larger view |
Once [x] Unblocked is clicked, this security menu disappears.
C. Create a Program folder to hold the program:
D. Copy the .exe to ProgramFiles\Util:
Copy/paste the downloaded .exe from the temporary/download folder to
C:\Program Files\Util (or directory of your choosing)
E. Create a Start Menu Tile:
Right-mouse-click the executable and "Pin to Start"
The program is ready to run. See icon on Start Menu.
Try it out:
1. Download and launch Midy5.exe
2. Open File-Explorer. Locate any file and click and drag it on top of Midy5
3. In all its glory, review the MD5 checksum
Version 1.04 - Added ctrl-N to launch Notepad. Added an Icon .ico file.
Version 1.03 - Added support for SHA-256
Version 1.02 - Tiny change to internal variable name. Small cosmetic change on panel.
Version 1.01 - Initial Release
Write this program yourself!
"War and Peace - Programming in C# Volume 6"
(Student/Instructor workbook, Project 4. Search Amazon.com for "War and Peace Programming")
Related links
keyliner wrote a command-line version of this same idea, except this version can view and inventory entire directories, showing which files have changed, which are new, or deleted. This utility was meant for volatile folders, usually in a corporate environment.
Link: File MD5 Checksum Inventory (batch MD5)
Link: keyliner file backup software
Leave a comment and tell me how you like the program.



No comments:
Post a Comment
Comments are moderated and published upon review. (As an aside, not a single spam has been allowed through; why bother?)