 Howto: Steps for removing the Boaxxe Win32/Cryptor Virus / rootkit from a Windows XP machine, using AVG, Malwarebytes, and other software. The Virus was successfully removed with these steps. Apologies on the length; this is a complicated subject. This article can be used for other viruses. Updated 2013.09.
Howto: Steps for removing the Boaxxe Win32/Cryptor Virus / rootkit from a Windows XP machine, using AVG, Malwarebytes, and other software. The Virus was successfully removed with these steps. Apologies on the length; this is a complicated subject. This article can be used for other viruses. Updated 2013.09. My daughter's laptop was infected with the Win32/Cryptor virus when she downloaded a music-sharing program. The infection's symptoms were typical: The PC became progressively slower and dozens upon dozens of "you have a virus" messages ("scareware") ultimately made the machine unusable. Once infected, traditional virus scanners cannot clean the infection.
See these Keyliner articles for other virus articles:
Microsoft System Sweeper - Bootable Antivirus - Start here. Highly Recommended
Removing Win32 Cryptor
Removing Win7 Anti-Virus
Removing Personal Security Virus
Securing Windows 7 from your Children
Microsoft Security Essentials
Although this article has been tailored to the Cryptor virus, these steps will work with almost all viruses and spyware.
This article receives numerous hits, indicating a lot of people do not have backups. I continue to make modifications to this article, using information from readers and from vendors. Please leave comments on how well these steps have worked.
Removal Steps
I decided to do the a'la carte method, and install individual free scanners and firewalls from different vendors. It took about five hours, not including research, to clean the virus, with most of the time spent waiting. Here are the steps used and if you want a guaranteed success, you must follow all of the steps, in this order. There were mistakes made along the way, described separately.
Some of the steps are somewhat risky. If your machine is running well enough, manually copy important data (photographs, checkbook files, novels, etc.) to offline storage.
0. Build a Bootable MSE disk.
Microsoft has a new Virus scanner that is very useful and I recommend following the steps in this article first. See this Keyliner article:
Microsoft Standalone System Sweeper
Follow the steps in the article to create a bootable virus-cleaning disk. Use it before attempting the remaining steps. Do these steps for all machines, Windows 8.x, 7, Vista, XP.
1. Pre-Download files.
On a non-infected computer, download the following programs and burn them to a CD (steps on how to burn are not detailed here; ask a knowledgeable friend to help, if needed).
If the download is Zipped, de-compress the Zip file.
For ease-of-use, place each downloaded program in a separate subdirectory.
The viruses are sneaky and can stop you from running known cleanup utilities. Because of this, the instructions will have you rename the vendor's files to a random name, described below; use any name you see fit.
Ideally, burn all of the downloaded files to a CD -- not a pen drive; media should be Read-Only.
Files:
Download Process Explorer: technet.Microsoft.com
On the page, search/Ctrl-F for "Process Explorer"
Rename ProcExp.exe to "WinLogon.exe"
Download RootRepeal: http://rootrepeal.googlepages.com/
Only download if using Windows XP or Windows Vista 32-bit.
The download can be found about in the middle of the page, under "static links".
- Click (download) the Zip version; select "Open file."
- Highlighting "RootRepeal.exe" in the opened Zip folder
- Other-mouse-click, select "Copy"
- Paste to your temporary directory
- Rename the pasted file to xxRootRepeal.exe (or other random name, including WinLogon.exe if in a separate directory)
Download ComboFix: ComboFix Download
*Only download if using Windows XP or 32-bit Windows Vista/7 ; not Windows 8
Rename to xxComboFix.exe
DownLoad SuperAntiSpyware: superAntiSpyware
Choose the Free Edition; this is a legitimate program, despite its flaky name.
Rename to xxSuperAntiSpyware.exe
Download MalwareBytes: Malwarebytes
Rename the installer to xxMBam.exe
Later, you will also have to rename the installed exe.
Burn these files to a CD.
2. Disconnect the infected computer from the Internet.
Unplug the Cat-5 network cable or press your laptop's function key/other key to disable wireless.
You do not want to be on the net while some of these steps run. I have found some of these virus cause too many problems while connected and this was the easiest solution. This will disable these programs abilities to download the latest updates; although this would be nice, the updates will have to wait.
3. Uninstall old virus scanners
If your existing virus scanners are old, obsolete or expired demo versions, un-install them now because they are not going to help and they can interfere with other steps. See Control-Panel, Add-Remove / Programs and Features.
However, some rootkit viruses will prevent you from entering the control panels. If this is the case on your PC, consider booting into Safe-mode (see below and try un-installing from there). Otherwise, continue with the next steps.
If you have McAfee Security Essentials installed (see Programs and Features), un-install.
4. Disable Existing Virus Scanners
If you have a current virus scanner, temporarily disable it to avoid conflicts. Since the machine is already infected, the virus scanner is not helping so it is safe.
See your vendor's documentation for exact steps on how to disable "real-time scanning," but here is a summary for many of the popular ones. Most programs have a system-tray icon to get to the correct menus.
AVG 8:
Open the System Tray's AVG8 Control Center, Tools, Advanced, in left-pane, scroll down to "Resident Shield"; deselect 'Enable Resident Shield'.
AVG 8.5:
Open the AVG Control Center; Double-click Resident-Shield; Deselect "Enable Resident Shield.
Avira:
"Other-mouse-click" the Avira System Tray Icon. De-select 'AntiVir Guard Enable'
F-Secure:
"Other-mouse-click" the system tray icon; choose "Pause Protection". Click "By User Request"
Microsoft Security Essentials (MSE)
Click Settings, Real-time protection; Uncheck "Turn on real-time protection"
McAfee:
"Other-mouse-click" McAfee System Tray Icon; choose Exit
McAfee Security Center 7.x:
Double-click system tray; click Advanced Menu, Configure, Computer and Files. Disable the VirusScan and the Internet & Network for Firewall.
Norton Antivirus:
"Other-mouse-click" System-tray icon; choose "Disable auto-protect". Set a duration of 6 hours
Norton 360:
"Other-mouse-click" system tray icon; choose 'Open Tasks and Settings Window'; Under Settings, click "Change advanced settings" Click 'Virus and Spyware Protection settings'; de-select 'Turn on Auto-protect'; Apply; choose "Until I turn it back on'
If you can't disable, consider un-installing before continuing; then re-install later.
5. Set Windows Screen Saver to None (disable the screen saver)
Some of these steps take a long time to run and the screen-saver impacts performance. If you are able to launch the Control panel, disable the screen saver with these steps:Windows XP:
-Other-mouse-click the desktop, choose Properties, [Screen Saver], set to None.
Vista/Windows 7:
-Other-mouse-click the desktop, choose Personalize, ScreenSaver
6. Boot computer in "Safe Mode"
Author's note: I am having problems with this step, depending on which version of Windows is installed. Originally, I had suggested to run as many of the next steps as possible in "safe mode, but I am finding many of the following programs do not operate in safe mode, depending if you are running Windows 7/Vista or XP.
My new recommendation: Skip this step. However, I am leaving it documented here because it can be useful with some utilities and has helped me in the past catch some viruses.
Original comments:
"With the infected computers I have worked on, everything was locked down by the virus and I could not open many Control Panel applets and overall performance was bad. For these reasons, I recommend starting the computer in a special Windows diagnostic mode, called Safe-Mode. The steps to open it are weird and may take some practice:
- Cold boot the machine (power off/on).
- Just after the BIOS splash screen, repeatedly tap on the f8 key (press insistently but not frantically).
- Choose Safe-mode, when prompted
- If you miss and Windows loads normally, reboot gracefully and try again.
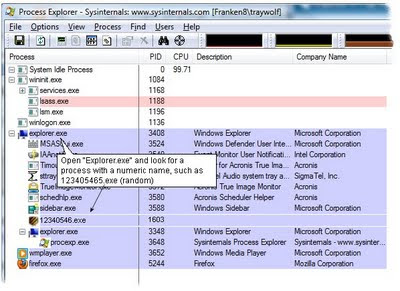
7. Run Process Explorer
This is a Cryptor-virus specific instruction. Skip for other viruses.
"Process Explorer" is a Microsoft program and it can sometimes stop the Win32/Cyrptor virus long enough to remove it. However, the latest versions of this virus elude this program, but it is worth a try.
a. From the CD, run D:\ProcessExplorer\WinLogon.exe (the renamed file) by other-mouse-clicking the file and choosing "run as administrator."
b. Scroll to the Explorer.exe section; wait a few moments and watch for program changes
c. Open the "Explorer.exe" section.
(Cryptor Specific step): Look for a program with a name such as "1234023.exe"; the name will be random. (It wouldn't surprise me if future variations of the virus use more legitimate-sounding names; study the list and see what program seems out of place.)
Note: Other rootkit viruses can live in this area. The key is to pay attention to unusual programs running in the Explorer section. It is normal to see multiple svchosts in this area and note that "procexp.exe" is this program. The Cryptor virus may show up in the list but newer versions do not.
If you do not see an obvious candidate, continue with the remaining steps.
d. Assuming you found a suspicious process, right-click the process and "Kill"
8. Install RootRepeal:
Follow this step if you are using Windows XP. For Windows Vista, 7 and 8, skip this step.
Before running this step, close all windows and programs on the computer -- including this browser page. You may need to write down these steps.
a. Copy xxRootRepeal.exe to a temporary directory (any) on the C: drive (this cannot run from the CD).
b. Launch the program by "other mouse clicking/right-click" and choosing "Run as Administrator". It will install; accept all the normal prompts; ideally, install in a different directory than the default one it recommends.
c. Once the program launches, select the bottom-tab "Files"
d. Select "Scan" and choose [x] the C:\ drive
The scan will take considerable time with *inconsistent* hour-glassing.
Wait for the status-bar message "Found xxx hidden/locked file(s)!"
e. Scroll down the list, looking for the C:\Windows\System32 or C:\Windows\System32\Drivers section.
The list will contain a mixture of legitimate and illegitimate programs.
Files in
C:\Windows\System32 or
C:\Windows\System32\Drivers
which are marked as "Hidden from the Windows API", will be the virus.
As of this writing, Win32\Cryptor reports as a .SYS filename, in the System32\Drivers area.
Other Viruses, such as the "Personal Security" rootkit, place a file called "C:\Windows\System32\Gather~1.xsl". In other words, look for any suspicious file with "Locked to the Windows API" in the System32 directory, as reported by RootRepeal.
The Win32\Cryptor virus will have a dot-sys (.SYS) extension and the name will be random (e.g. UACewsflctd.sys). The name can be long or short. Here are example names but it will be the only .SYS extension in the System32/drivers directory:
TDSSspax.sys
TDSSServ.sys
GAOPDXserv.sys
gaopdxohocrlokojvgccmieiquramguxlachqk.sys
UACmxegjtve.sys
UACd.sys
Senekarstpqyy.sys
ovfsthxkwpjtxfk.sys
kungsfxwrtceey.sys
SKYNEToyfjtpeo.sys
MSIVXwfjwbpbivasavbfjmtkibegxvnftiqxt.sys
(Don't be surprised if future versions of this virus use more legitimate-sounding names.)
f. Highlight the offending file, other mouse-click and choose "Wipe File".
Unfortunately, there is no indication this step succeeds; trust that it did.
g. Important: Immediately select Start, Shutdown and reboot the computer; do not close any programs. Reboot back into Safe Mode, as described above.
If you do not find a likely name, you may be infected with a different Root-kit virus.
9. Run ComboFix.exe (xxComboFix)
Windows XP users: ComboFix is also a root-kit cleaning program for a different vendor. I also like to run it because they sometimes see programs that RootRepeal misses.
a. Close all programs, including this browser. You should be in Safe-Mode
b. Other-mouse-click the exe and select "Run as Administrator".
While it runs, it may need to install Microsoft's Recovery Console; allow this to happen. Do this by plugging in your network cable / turn on wireless; wait about 1 minute for the connection to establish; then click OK.
The scan process takes 10 to 20 minutes, depending. You may notice various black screens. Be patient.
It will reboot; come back up *without using Safe-Mode.* It will then take about 10 minutes to generate a log file. Your firewall may spring to life, prompting for pev.cfxxe -- this is a ComboFix program and allow it access to the Internet.
After the program runs, they recommend uploading your log-files for further review (see C:\Combofix.txt). You can do this if you like but I recommend continuing with the next steps. The displayed Log file will not be that interesting.

Assuming the RootKit Removal programs did their job, it is now time to remove the other viruses that are probably lurking in your system (cryptor installs other viruses, just to be mean).
10. Run SuperAntiSpyware
Despite its flaky-sounding name, this is a great program. To run, follow these steps:
a. If needed, reboot the computer; you cannot be in Safe Mode when running this program.
b. Locate the Renamed program; other-mouse-click; "Run as Administrator"
c. Accept the legal agreements, etc. Install in a different folder than recommended. I recommend choosing C:\Program Files\Util\SuperAntiSpyware
d. Accept various installation options, as you see fit; optionally allow it to send a diagnostic report.
e. Run a *Full/Complete* scan.
Allow it to reboot if it finds anything.
11. Install and run the renamed MalwareBytes program.
Despite its scary name, this is a legitimate program. For now, *do not* allow it to check for updates (I found this virus caused too many problems if the Internet were active).
a. Install the program by double-clicking the renamed exe file.
b. When prompted, choose a different install directory.
I recommend C:\Program Files\Util\MBam
c. Once installed, use Windows Explorer to locate the installed files:
See C:\Program Files\Util\MBam
Rename MBam.exe to "xxMBam.exe"
d. Launch the program (xxMBam.exe); allowing it to run. Under "Scanner", choose Full-Scan. Allow the scan to run. It will be time consuming.
e. Reboot gracefully once the scan completes.
By this stage, the Virus should be cleaned. Continue with the remaining steps.
11a. If you still suspect a virus
Plug in the network cable/wireless and re-establish a connection to the internet. Allow MalwareBytes to update to their latest version. Once it updates, you will have to re-re-name mbmam.exe to a new name, such as 123Mbam.exe. Re-run that step as "administrator."
12. Download and install a new Virus Scanner, if neededIf you still have an existing virus scanner installed, re-enable the program and run a full-system scan.
If you do not have a virus scanner, download and install one of the following free scanners (they also have commercial versions). I no longer recommend any commercial vendors. Although not the best, consider using Microsoft's MSE program (also free):
Microsoft Security Essentials (a new, free virus scanner "MSE")Avira
AVG's Free AntiVirus
(Shift-click the link(s) to open the download page in a new window. Choose and install only one of the above)
(If installing AVG, be sure to download the Free version, which is different than the Trial version. It may take a moment to find it. As of 2009.09, the AVG link above takes you directly to the correct site. Here are detailed instructions on how to best install AVG in order to avoid a performance bug they have: AVG Detailed Installation Steps)
With my daughter's computer, AVG detected 12 additional spyware and viruses but like Microsoft's product, these cannot clean RootKits. On another computer, infected with Win32/Vundo.B, MSE detected, but was unable to clean an already-installed virus.
13. Uninstall likely Viruses
Using Windows Control Panel, "Add-Remove Programs" or Windows 7 "Programs and Features", un-install p2p programs such as uTorrent, Bittorrent, LimeWire, Morpheus and others. These are typical sources for spyware. Take the time to delete other programs and toolbars you no longer need.
14. Delete all old Restore Points (they may be infected)
a. Launch Windows Explorer, other-mouse-click the C: drive.
b. In the [General] Tab, click "Disk Cleanup"; click "Cleanup System Files" (Windows 7), click top-tab "[More Options].
c. Click "Clean up" on the System Restore and Shadow Copies. Allow it to delete all but the most recent restore point.
Success!
These steps cleaned the virus and this article has been fine-tuned to give the best-to-date results. The steps may be over-kill, but they should clean the machine.
Consider giving a financial reward by sending a donation to the good folks at MalwareBytes and SuperAntiSpyware -- they are doing you a great service.
This is a good time to make a full-system backup. See this article: Using Acronis.

Mistakes in the Process: AntiSpyware
During my research, I was a fool and downloaded and installed www.antispyware.com. Antispyware came recommended on several discussion threads and it was free. As it installed, it asked for my name and email address, ostensibly to send a license key. I was suspicious. Why does a free program need a license key?
I quickly built a new junk Email address and used it to register. As soon as I clicked OK I knew I was in trouble -- the program installed, then detected a variety of bogus viruses -- and then asked for $50 in order to clean them. I had been duped. I was glad I registered with a fake email. I un-installed the program. If I would have provided a credit-card number, I would have been in deeper trouble.
Further research showed a lot of people happy with this program and a lot of others saying it was a scam. With mixed reviews like that, something is up. I suspect the happy people were plants.
MalwareBytes identified this as spyware and removed it. I learned my lesson: Search the net before committing to any product.
Do not confuse this program with a legitimate program, "superAntiSpyware" (which has a free and paid version.)
Manual Removal Steps:
Several have asked about manually removing Crytor. There is no manual way to remove a rootkit virus because, by their very nature, they hide in areas not visible to standard software. Of the dozens of sites I found that claimed to have the steps, I found most were flawed and often the steps fell apart half-way through the instructions. In the end, these sites hoped you would become frustrated and would then sell their removal product. I suspect some of these sites were written by the original virus authors.
Other Observations:
My daughter's computer had a three-year-old virus scanner, with current signatures, but this was not adequate to stop this virus from entering into her computer. There is no doubt that she should have had a newer scanner, but even that is no guarantee; poor surfing habits are hard to defend against.
From my previous article (see here), I have not been not impressed with any of the major vendors. In the end, I decided to try AVG's virus scanner. But AVG has been problematic. On three separate computers, the AVG engine hogs too many resources. After you complete these steps (including AVG), look at this article to determine if AVG is behaving. If you find AVG occupies 20 to 100% of your CPU resources, follow the steps in that article.
If you use AVG, be aware it also has a spyware scanner (that cannot be disabled) and it may conflict with Windows Defender and MalwareBytes.
Since this article was originally written, Microsoft released a free virus scanning software, 'Microsoft Security Essentials' (MSE) that is worth trying. On an infected machine, this scanner has detected viruses, but seems to have trouble cleaning them -- requiring a reboot after each virus is detected.
When a machine is infected with multiple viruses, this adds to the time. I suspect the program behaves better if it were running before the infection but I installed after-the-fact.
MalwareBytes free version is not a real-time program and runs only on demand. But with a purchased upgrade, the program runs in real time. The fee is a reasonable ($25) for a non-commercial, perpetual license, which is an honest price for an honest product. If you go this route, uninstall other virus and spyware scanners. This program, especially the free version, is I program i trust.
Be sure to update Java and Acrobat Reader to the latest versions; both had flaws that were easily exploited by other viruses.
Final Recommendations:
This was a mess and it took hours to clean up. A far better solution is to make a disk-image (ghost) of the entire computer prior to the virus. Buy a cheap external USB drive and run a program like A*cronis or Maxtor's USB program. You can read about this idea in this article: G*host vs A*cronis.
See these Keyliner articles for other virus articles:
Microsoft System Sweeper - Bootable Antivirus - Highly Recommended
Removing Win32 Cryptor
Removing Win7 Anti-Virus
Removing Personal Security Virus
Securing Windows 7 from your Children
Microsoft Security Essentials
Cleaning a Virus
G*host vs A*cronis
Maxtor USB External Drive
Configuring Windows Firewall for Outbound Traffic
Vendor Links and Products mentioned:
Microsoft Process Explorer: http://live.sysinternals.com/procexp.exe
RootRepeal Rootkit Killer
ComboFix
Malwarebytes (manual rename) Malwarebytes (random named)
Malicious Software Removal Tool
Other Products of Interest:
Mcafee "Stinger" Removal Tool (a batch removal tool; useful for some viruses)
VirusTotal (single-file Analyzer using 30 different scanners)
HijackThis By Trend Micro
Java (Updated/Install)
Acrobat Reader (install/Update)
The Win32/Cryptor is also known as okbjivb.dll, Win32/Alureon.gen, Generic Downloader.x, VirTool:Win32/Obfuscator.CT, Downloader.MisleadApp, Backdoor.Tidserv.
Please leave a comment (no registration required) on how well this article helped with your virus problem. This will help other people understand how successful these steps were.

Hi,
ReplyDeleteThis is a request for some advice (or a miracle would be great too).
I ran avg first because I hadn't found this post. It it found 100 infected files, 3 of which were spyware and 97 of which were viruses. Avg removed the spyware and 3 of the virally infected files but I couldn't get it to remove the other 94 infected files.
At this point I found your post.
I tried system restore, which didn't work.
I then proceeded to download and run Malicious Software Removal Tool which found and got rid of one virus.
I skipped the AVG run because I had done it previously.
I downloaded, renamed, and ran the Malwarebytes file. During installation it tried to find:
C:\SWSETUP\EISU\HpSdpApp\
but couldn't because it was supposedly on a network resource that was unavailable, but it somehow finish installing without it.
The .exe files were renamed and I tried running but then it tried and failed to find the same file as above. So now I'm stuck. Can you recommend a next step?
Thanks,
Response to Teabag:
ReplyDeleteSystem Restore Not working: No real surprise and I hope my article expressed my lack of faith in that step. In any case, it couldn't hurt to run it. More on this in a moment.
The HDsdpapp is an HP Printer program that can be removed. If you are familiar with the registry, remove it at this key
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
or Start, Run MSConfig and remove it from the startup files. If you are curious, HP has this article about this program. It appears their program may be malfunctioning, and this is another reason to remove it.
From your email, I was unsure is Malware bytes ran successfully or not (you implied it ran but did not find the HP file.... If it ran successfully and didn't find anything else to clean, then this would be good news. Not knowing the exact order you ran your steps, the System Restore may have returned many infected files back to a non-infected state and other anti-virus steps may have cleaned other files. All of this might explain why it did not find this same file (or others). Again, this would be good news. Also, if the virus program updated themselves, they may have removed a false-positive.
Knowing when the viruses are fully removed is tricky and this is why my article recommends running multiple different programs. Confirm each program is up-to-date and try running AVG again. If all report no problems, then you may be done.
Write me again with more details, if needed.
Once you get the machine cleaned, consider an external USB backup drive
See my previous article: Maxtor USB Drive
or more sophisticated software, such as Acronis vs Ghost. (Sorry I can't link to these in this message)
Thank you for the response. Just to wrap up the story, my brother ended up running Spybot - Search and Destroy followed by AVG, and this seems to have gotten rid of the virus. Malware installed but even after renaming, I could never get it to actually run.
ReplyDeleteA external backup drive is definitely in the works.
Cheers,
Tim, I followed your instructions to the letter. Yes it did take quite awhile (as you indicated it would), but the advice was well worth the effort. This was a particularly nasty program that thwarted the usual deletion efforts. Still not sure how it first got into the system, but with teenagers, anything is possible. My thanks for sharing the fruits of your labor with the rest of us!
ReplyDeleteWould just like to say that process works, to anyone wondering. It took me the better part of a day in all to get through everything. But, as far as I know, it has fixed all the issues related to this. Kudos to whosoever figured this out. Normally I take care of viruses/trojans/worms/whatever on my own. But this one was particularly resilient. Don't take shortcuts, it's a pain in the ass.
ReplyDeleteNice work Tim! Thank you for the info and time spent on this. I was on the verge of admitting defeat until I ran across your post. It worked like a champ! Much Kudos to you Sir. I'd never used RootRepeal before, nice little program! On a side note, I also wiped the UACxxxxxxxxx.dll's that were hidden in the windows\system32\drivers folder. Something else I ran across was that Corel Suite 8 has some hidden UACxxx files that I left alone. After an AVG, a SuperAntiSpyware, Malwarebytes, and IO Bits Security 360 scans, the PC is looking clean. One other thing I was considering is trying AVAST home edition and scheduling a boot scan. I found that works well on infections. Thanks again!
ReplyDeleteBy chance, my Nephew's computer was infected with a different rootkit: Win32/Vundo.B and Win32/Vundo.Gen.G.
ReplyDeleteThese steps also cleaned the virus. Of interest, Microsoft's new MSE detected the viruses, but hung the computer when it tried to clean them - indicating it probably would have prevented the infection if it were installed pre-virus.... but the cleanup failure was disheartening.
(Sadly, MSE also failed to detect Trojan.FakeAlert and Adware,MyWebSearch)
With the Vundo.B, It took a lot of coaxing to get MalwareBytes to run and I've enhanced the steps above to account for this. Once again, Malware saved the day. I wonder how their real-time scanner works?
I'm going through the steps to remove the cryptor virus on my other computer. I've downloaded and run Process Explorer, but I don't see anything in the explorer.exe section that I can't identify as a valid process. What now? Should I go ahead and download RootRepeal and continue from there?
ReplyDeleteAnonymous (ProcessExplorer): I believe the latest versions of Cryptor use legitimate-sounding names; check the list carefully.
ReplyDeleteIf still not found, I suppose you could continue with the remaining steps. If the virus is still installed, it won't let MalawareBytes even load -- if this happens, this is your hint to look at Process Explorer more carefully. If you are still stuck, send me a screenshot (see About) on the right-side of this blog.
Fantastic. Took one afternoon in total and followed every step to the letter - success!
ReplyDeleteFirst class, thank you.
JD: Without an internet connection, you will never get the virus cleaned. From another computer, download (and expand) all needed software; then Burn to CD (not a thumbdrive).
ReplyDeleteTry running all cleanup steps from the CD -- this might even be a safer way to clean all viruses because the virus can't monkey with the other programs.
I'll experiment with this idea in the future.
Wow it works. I blundered through your procedure in my usual inept way with some stages not 100% as you suggested but I carried on regardless and I seem to have a clean machine again. Excellent procedure. Nice work and thanks. Dave.
ReplyDeleteThe author writes: I have updated this article with (hopefully) more streamlined steps. I had the chance to use these same steps for another infected machine and I was again successful. Bad surfing habits...
ReplyDelete