Corporate servers often have processes that generate temporary files and those files sometimes need periodic deleting. Classic examples include
- Fax Server sent-fax folders
- Medical Image Gateways and other image processing servers
- Sharepoint Log files in the bin\12\logs folder
- Temp directories, etc.
 The issue is this: Deleting files is easy. It is harder to delete files older than (30) days and logging what was deleted is even more troublesome. Bulldoze does all of this, and it runs unattended.
The issue is this: Deleting files is easy. It is harder to delete files older than (30) days and logging what was deleted is even more troublesome. Bulldoze does all of this, and it runs unattended.
Free download.
No Adware, no spying, no registration, no email required.
Does not call the mother ship; does not need an internet connection.
Just download and run.
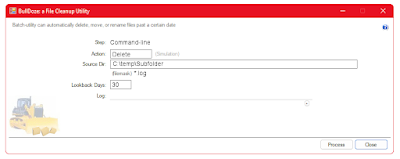 |
| Click for larger view |
BullDoze Features
BullDoze.exe is a compiled program that has the following features:
- It can Delete, Rename, Move, or MoveRename files
- Triggers on a file-age; files older than xx-days
- Can identify and delete millions of files
- Optionally, aged files can be moved to a different (backup) directory
- Command-line-driven
- Auto-starts, runs, then auto-closes
- The process can be run any number of times, against multiple directories
- Full Logging is supported. Each process can log independently or all logs can be combined.
- Schedule-able with Windows Scheduler or other
- No installation required; No registry entries
Installation:
To install this program, download the .exe and place in any folder on
your hard disk.
Double-click the .exe to run - no installation
required.
Since keyliner cannot afford a signing certificate,
you will be prompted that the file is not safe (being downloaded from
the internet). Click "more information" and allow the program to run.
Follow these steps for a more professional installation:
Copying
the .exe from a download folder to a folder in your "Documents" folder
is a quick work-around for other Windows security issues, but is an
inappropriate place to put software. Instead, it should be copied to
Program Files so it gains the protection of other Windows security
features.
A. Create a Program folder to hold the program:
Using File Explorer, open folder C:\Program Files
Create a folder C:\Program Files\Util
B. Download the .exe to a Download or Temp folder:
From Keyliner's public GDrive, click this link and download to a local temp or download directory. Do not download directly into ProgramFiles.
keyliner's public GDrive Download Link:
BullDoze on Keyliner GDrive.
MD5: 67-67-89-3e-8b-39-5f-d5-d7-07-f5-57-a9-9b-6f-69
SHA-256:
7645f44e8c9ff2d424ed1aa1337fe5fca145e71f7d8594b77d5705b1feb85a8a
When downloading, different browsers behave differently.
You will be prompted the file cannot be scanned. Click "Download anyway"
Microsoft Edge:
Prompts "BullDoze.exe" was blocked because it could harm your device.
"Click See More" and allow the download. With Edge, the file will appear in your Downloads directory with a random name, "Unconfirmed 780359.crdownloaded" (name varies).
Rename the file to "BullDoze.exe".
C. Mark the program as safe-to-run:
(This step may not be needed if downloaded by Edge and you clicked "More / Download Anyway")
Using File Explorer, right-mouse-click the downloaded (and re-named) .exe
Select "Properties"
Check [x] Unblock. This removes the "mark of the web."
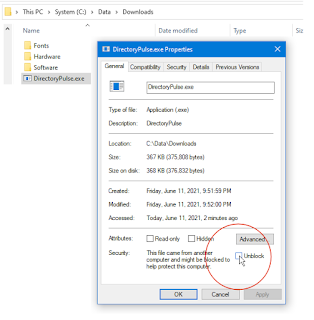 |
| Click for larger view |
Once [x] Unblocked is clicked, this security menu disappears.
You may be prompted for security UAC/Windows credentials.
D. Copy the .exe to ProgramFiles\Util:
Copy/paste the .exe from the temporary/download folder
to C:\Program Files\Util
E. Create a Start Menu Tile:
Right-mouse-click the executable and "Pin to Start"
The program is ready to run. See icon on Start Menu.
Generally, BullDozer.exe is copied to a UTIL directory, or it can be placed directly in the directory you wish to cleanup (it never deletes itself or its own control files).
Command Line Parameters
BullDoze must be launched using command-line parameters and is not meant to be run interactively.
The reason this is a command-line-driven application and for safety, once launched, you cannot enter or change parameters on the screen. This program is capable of deleting large swaths of disk, and for this reason, it must be launched deliberately.
It can be run with all parameters typed on single command, or it can call an INI file, which can contain one or more separate command-steps.
Example Command Line:
BullDoze.exe Action=Delete SourceDir="C:\Temp" Files="*.*" Days=90 LogResults=Y
where all files older than 90 days, any extension, will be deleted from
C:\Temp. Results are recorded in the current directory in file
"BullDoze.log". This is typed as a one-line command and can be placed in
a batch file or in Windows Scheduler.
Optional parameters are in italics:
Action=DELETE, RENAME, MOVE, MOVERENAME
SourceDir="directory\path"
Files="*.*"
Days=nn | Days=-1 to delete all files unconditionally
LogResults=y/N | LogResults="C:\path\filename.log"
AppendLog=y/N
DestinationDir="directory\path" (if using MOVES)
Overwrite=y/N (Allow overwrites on Moves/Renames)
Comments:
- All parameters are keyword=value pairs. e.g. Action=DELETE
- Parameters are not case-sensitive
- Embedded spaces are not allowed unless enclosed in quotes. e.g. SourceDir="C:\Test folder\directory"
- Do not use spaces as in (Action = Delete)
- Source and Dest directories can be \\server\path names
- Client must be pre-authenticated to remote servers
- Bulldoze runs as the current user; use Windows Scheduler to run with different credentials
Bulldoze.exe C:\data\myBullDoze.ini
Instead of a long command line, which is limited to just one delete transaction, an INI file can have two or more separate delete steps, and each step is given a cosmetic name. Here is a sample INI file:
;BullDoze Command INI file
[General]
AppendLog = N
LogResults = C:\temp\testLog.log ;Y/N or a filename
StartupTimerCount = 4 ;Delay in seconds before
launch; 0 to disable
VerboseLogs = Y
SimulateSteps = Y
Diagnostics = N
[CommandLine-like Example] ;cosmetic step name
Action = DEL
SourceDir = C:\data\test
RecurseSubDirs = N
DeleteDirs = N
Filemask = *.* ;(Filemask *.* assumed if blank)
Days = 14
DestinationDir =
Overwrite =
[SimpleFileDelete, Do not traverse Subdirs] ;cosmetic step name
Action = Disable
SourceDir = C:\data\Test
RecurseSubDirs = N
DeleteDirs = N
Filemask = *.dork
Days = 15
DestinationDir =
Overwrite =
Typical Use:
From a server, open the Control Panel, Scheduler
Add a new task, calling BullDoze.exe.
While building the schedule, click Advanced properties, and add the parameters.
Let Windows Scheduler run the program once per day. Details on this step needed; sorry.
Parameters:
Action=Delete
In-use, write-protected, insufficient-rights, files are not deleted. Failures are recorded in the (optional) LOG file and will not cause the program to fail.
Action=Move
Requires a DestinationDir.
If the file already exists in Destination, it will not overwrite unless "OverWrite=Y" is explicitly stated.
Action=Rename
Renames the file, leaving it in the current directory.
Renames are OriginalFileName_yyyymmdd_hhMMss.ext
If file has already been renamed within the same day, it will not attempt a second rename unless OverWrite=Y.
Rename with date-time stamp is the only option supported at this time.
Failed Renames are logged.
Action=MoveRename
Moves the file to the DestinationDir and renames, following the same rules, described above.
SourceDir=
Path must pre-exist
Path can be in the form "C:\path\path" or "\\server\share\path"
Quotes should be used on all paths; required if embedded spaces
If server path, client must be pre-authenticated prior to running BullDoze. This will be a future enhancement.
Do not use file-masks in the SourceDir (see Files=)
Generally, the SourceDir is on the same machine as the program.
Files=*.*
Standard DOS file masks are supported.
Examples: *.* All files eligible
*.LOG only (delete) Log files
2009_*.LOG, etc.
DestinationDir=
Required if MOVE or MoveRename
Days=nn
Specifies the age the file must be, in days, before the action is taken.
e.g. Days=30
Use Days=-1 (no spaces) to delete all files, regardless of age.
Days=0 is illegal.
LogResults=y|N
If not specified, results are not Logged.
If LogResults=Y, a default log file (BullDoze.Log) is created in the current DOS directory.
If LogResults="C:\Filename.exe", "Y" is assumed and this log-name is used.
Log files can be stored in the SourceDirectory and are not deleted.
Log Files are a standard ASCII text file, viewable with Notepad.
Subsequent runs overwrite the log file, replacing the older copy, unless AppendLog=Y.
AppendLog=y|N
If AppendLog=Y, log entries append, newest last. Caution, log files can get large. This utility will not manage its size and it can grow very large. Use with caution.
OverWrite=y|N
During a Move or Rename, if the destination file already exists, it will be overwritten if this switch is set to Y. Otherwise, the file fails and is logged. Generally, all MOVES and RENAMES should allow overwrites.
Update:
Version 1.01 - 2022.05 Re-compiled using Visual Studio 2022 and dotNet 4.8
Version 1.00 - 2019.12 Initial Release
Suggestions are welcome. I'd like to know if you use the program, drop me a note here on this blog.
Keywords:
auto-delete
automatically delete old files
cleanup old files
bulldozer file-delete


















 In older versions, this was found in the Database Utilities Menu.
In older versions, this was found in the Database Utilities Menu.